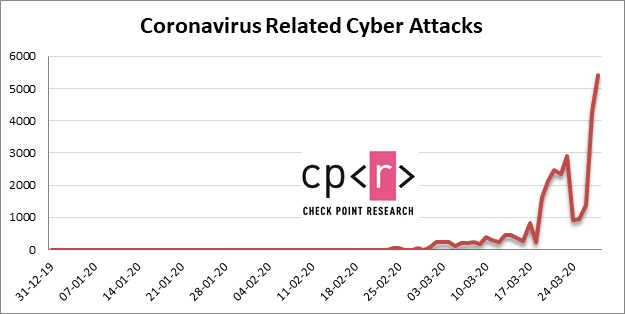
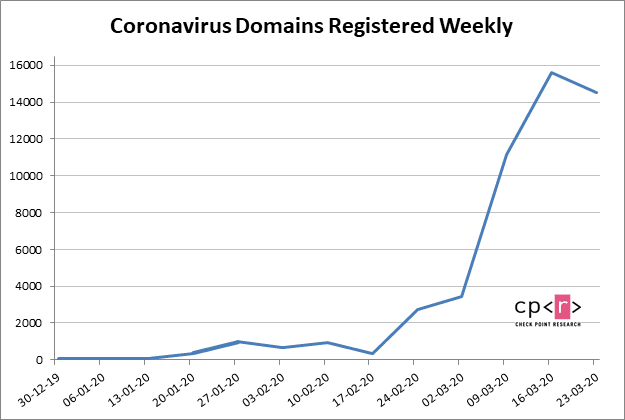
Since mid-February, researchers at Check Point have seen an escalation in the number of these attacks from a few hundred daily, to more than 5,000 on March 28 alone. We’re now seeing more than 2,600 attacks per day on average. The following graph represents all coronavirus-related attacks based on ThreatCloud, Check Point’s threat intelligence engine. Credit: Check Point For these purposes, coronavirus-related attacks are understood to mean any website with “corona” or “covid” in the domain, as well as files with “corona” or related file names. Additionally, researchers looked for coronavirus-related subject lines in email. In the last two weeks alone, more than 30,000 new coronavirus-related domains have been registered. Only a small percentage of those (0.4% or 131) were deemed malicious, with a handful more (9% or 2,777) being considered suspicious and requiring additional investigation. Since January 2020, more than 51,000 coronavirus-related domains have been registered. Credit: Check Point One popular way hackers are cashing in on the pandemic is by piggybacking on the success experienced by stay-at-home products and services, like Netflix. Due to quarantine-related measures, more people are staying home than ever before — meaning Netflix gets to cash in on those looking for ways to stave away boredom. Hackers have taken notice, building phishing sites meant to fraudulently acquire users’ credit card numbers by using official-looking domains, such as netflixcovid19s.com. As for how to protect yourself, the same rules apply as always: double check website addresses to look for misspellings or anything else that seems slightly off; be wary of opening emails, especially those with attachments, from an unknown sender; and be sure you’re buying products from reputable sources, not an email link — Check Point suggests googling the product or retailer and buying from them directly.